Why Expertise Is a Top Consideration When Considering a GRC Partner
GRC is an ever-evolving practice; place value in a vendor with extensive knowledge of the GRC landscape, one…
What’s the surest way to lose a board member or executive’s attention, right at the crucial moment where you’re making the case for further support for or investment in your cybersecurity programs? Show them either dense spreadsheets with lots of esoteric information or vague, colored charts — neither of which are specific or clear enough to tell them which cyber threats pose the greatest risk to the organization.
The sad fact is that this is exactly how many cyber risk teams currently handle reporting to leadership and their boards. And that makes it so much harder to get the buy-in you need from the people you need it from to harden your cyber defenses or seize on risk opportunities that could generate strategic advantage.
All of that can be solved by finding ways to communicate cyber risk to business leaders in a common language that they can all understand: financial impact. Fortunately, there’s a tried-and-true way to do just this, and it’s called cyber risk quantification.
This article will explain how you can leverage cyber risk quantification to build a business case for taking cybersecurity risk more seriously and giving cyber risk programs the support they deserve.
Risk quantification is the process of calculating the potential loss frequency and severity of a particular risk and translating it into financial terms. Cyber risk quantification (CRQ) is simply the same process, but applied specifically to cybersecurity risk. Risk quantification has been around for a while, but there’s been a much heavier focus on applying it to cybersecurity as cyber threats grow in number and evolve.
The benefits of being able to present your organization’s cyber risk in the context of real business impact — especially financial impact — are myriad:
For a deeper dive into all the ways embracing cyber risk quantification can help you make the business case for more support for cybersecurity programs, check out our e-book, “Building the Business Case for Quantifying Cyber Risk.”
So, you’re convinced that cyber risk quantification is the future of cybersecurity risk communication and prioritization. But how exactly is it done?
Let’s dig into the steps you’ll need to take to start building a scalable, repeatable, and efficient cyber risk quantification process.
The first step to quantifying your cyber risk is understanding which cyber risks you’re actually facing. Without that information, you’ve got nothing to tie any financial figures to.
Make a list of all the different adverse events that your organization could potentially face based on stakeholder and subject matter expert interviews, data analyses, review of external media, and other sources of information.
With your list of cyber risks in hand, you can start to map out all the areas your organization is vulnerable to each risk and the adverse outcomes it carries. A good way to do this is to start from the adverse outcome. What events would need to happen, in what order, to lead to that outcome? There’s your vulnerability map.
Make sure you also evaluate and map all the controls you have in place to mitigate your cyber risks, too.
Now we’ll really get into the meat of cyber risk quantification: actually pegging some monetary figures to each of your cybersecurity risks.
There are multiple ways of going about doing this, and having the right frameworks and cyber risk quantification software in place can go a long way in helping you carry out your analyses.
Using a consistent framework to measure risk streamlines the process and helps make sure everyone carrying out the work is on the same page. We recommend leveraging these common, tried-and-true approaches:
Open FAIR is a standardized framework for quantitative analysis of cyber risk. First released in 2006, it’s one of the most common frameworks for risk quantification in use today.
The FAIR model takes into account all of your assets and the threats facing your business, then runs thousands of simulations to determine the estimated financial impact that each threat could carry. It takes a variety of inputs, illustrated below, and returns a range covering the minimum and maximum value of loss for a specific risk scenario and the most likely value you stand to lose in a year if the risk materializes.
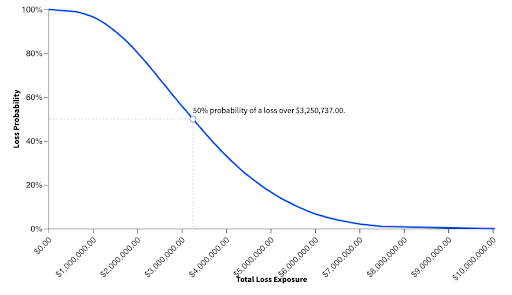
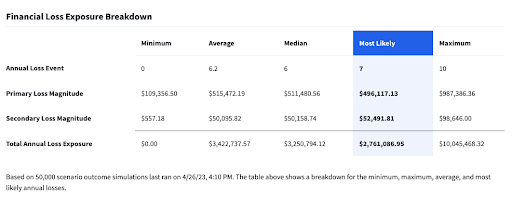
Monte Carlo simulations are the type of simulations that the FAIR model runs under the hood. These simulations run repeated random sampling to produce estimates of the value of loss a risk could carry. They return two outputs: a loss exceedance curve that shows the percentage of the simulations that met or exceeded a given amount of loss in one year, and a table showing the probable frequencies and magnitudes of the loss events:
Together, these outputs provide the most accurate estimate of the amount each risk could cost your organization, allowing you to more accurately rank and address them. Having risk management that is capable of leveraging both of these techniques in place can help you automate these analyses on an ongoing basis and automate the process.
Named for its resemblance to the clothing accessory of the same name, bow-tie analysis is a risk visualization technique designed to help you to map adverse risk events to their triggers and their end results. Visualizing risk this way lets you offer an at-a-glance explanation of how a risk event might occur and what the consequences would be.
Open FAIR and Monte Carlo simulations can stand perfectly well on their own as cyber risk quantification methods, but they’re even more powerful when combined with one or more of the many existing cyber risk management frameworks in use today. Taking this approach ensures that you’re not only complying with widely-accepted and proven standards for managing cybersecurity, like NIST, SOC 2, and ISO, but that you’re putting hard financial figures behind them every step of the way.
The NIST Cybersecurity Framework is a cybersecurity and cyber risk management framework published by the U.S. National Institute of Standards and Technology. It is designed to provide businesses and organizations with a flexible process for identifying, assessing, managing, and mitigating cyber risk.
The NIST framework rests on five pillars, each of which can benefit from cyber risk quantification:
Identify: Cyber risk quantification is most helpful in this phase. This is where your quantified risk data can tell you which cyber risks are the most pressing.
Protect: In this phase, CRQ can help you best allocate your cybersecurity resources to defend against those most important threats you identified in the Identify phase.
Detect: Each time new cyber threats are detected, you can quantify the risk associated with them to see whether they warrant more or less attention.
Respond: Cyber risk quantification data can help you best decide your course of action when responding to a cyber event. Does the event carry a significant cost that warrants aggressive action, or is it a trivial event that can be handled more easily?
Recover: In this phase, you’ll be able to use your quantitative data to understand how much was lost, and why, so you can bolster your defenses for the next time a similar risk event occurs.
SOC 2, or Service and Organization Controls 2, is another cybersecurity framework designed to help organizations safeguard their sensitive assets and data from cyber attacks and breaches. It also has five pillars: security, availability, confidentiality, privacy, and processing integrity. There are also two types of certification: SOC 2 Type I, which consists of a single audit within a specific time period, or SOC 2 Type II, which involves ongoing audits to show compliance over the long run.
Like most voluntary cybersecurity frameworks, organizations that attain SOC 2 compliance certification can use that status to assure clients, investors, and other stakeholders of their security practices, which can become a competitive advantage. One of the most accurate and easiest ways to provide SOC 2 auditors with the information they need to determine your organization’s compliance with the framework is to offer them robust data, and cyber risk quantification is one of the best ways to provide this sort of evidence.
ISO 27001 is considered one of the highest international security standards for cybersecurity. Like NIST and SOC 2, it’s designed to provide a proven framework for managing information security risk, but it differs in that it’s a globally-focused standard, not a U.S. specific framework, but cyber risk quantification can benefit this framework in the same ways as the previous two.
Nothing causes glazed-over eyes or confusion as quickly as a massive grid of numbers on a presentation slide or a dense, multi-page report stuffed full of long paragraphs and those same spreadsheet exports.
That’s why it’s important to use clear, concise formats — ideally, short lists or charts and simple visualizations — to explain only the most important, pressing risk insights you were able to draw from your analyses. Since you’re using hard numbers, not vague charts, you’ll still be able to drive home the impact of your biggest risks without getting into the weeds of every cyber risk facing your organization.
None of the hard work you put into your cyber risk quantification efforts will be worth anything if you don’t put it all into action somehow. Here’s a quick five-step action plan for using your cyber risk insights to improve cyber resilience and security across your organization:
While risk data can be quantified manually, this is a time-consuming process that can be vulnerable to human error. A much better way to quantify cyber risk is by leveraging a modern GRC platform with risk quantification capabilities built in, like LogicGate Risk Cloud and its Risk Cloud Quantify feature.
These integrated risk management platforms are designed to centralize all of your cyber risk in one place and automate the process for adding additional risk information into your repositories, making it all readily available to the quantification feature. This way, you can run automated cyber risk quantification on a continuous basis.
SOC 1®, SOC 2® and SOC 3® are registered trademarks of the American Institute of Certified Public Accountants in the United States. The AICPA Trust Services Criteria for Security, Availability, Processing Integrity, Confidentiality, and Privacy is copyrighted by the Association of International Certified Professional Accountants. All rights reserved.
GRC is an ever-evolving practice; place value in a vendor with extensive knowledge of the GRC landscape, one…
At LogicGate, we are proud to recognize the remarkable women who are not only making waves within our…
Whether you’re looking to win new business as a vendor or mitigate risks as a customer, vendor security…